Why a Tech Assessment Is the First Step on Your IT Roadmap to Compliance and Security
When you’re responsible for protecting sensitive data like customer records, financial information, or patient files, the margin for error is razor thin. Regulations are strict, cyber threats are relentless, and your IT resources are already stretched thin.
You know security and compliance aren’t optional, but where do you start?
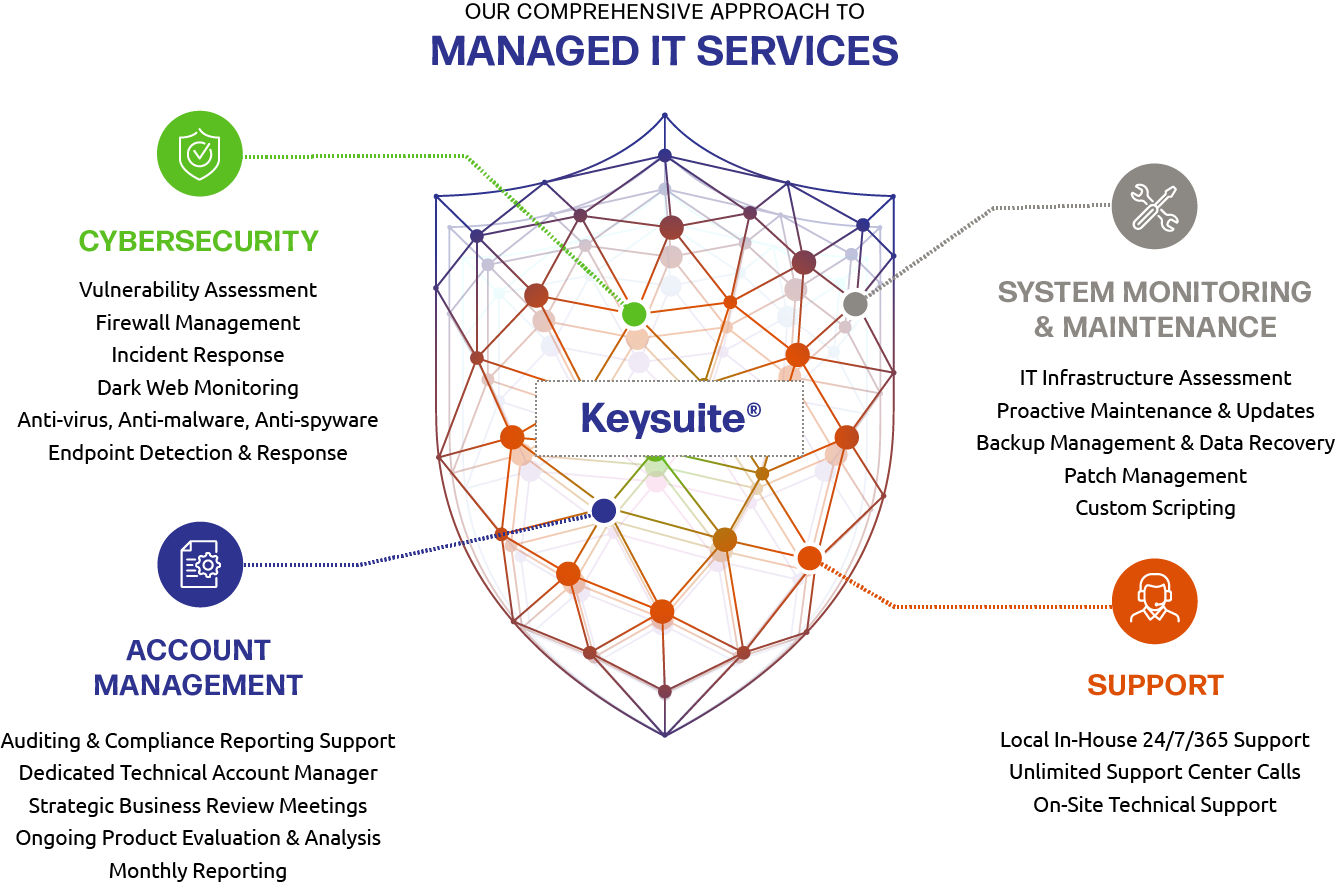
The smartest first move isn’t buying another security tool or rewriting policies from scratch. It’s understanding exactly where your technology stands today. That’s the power of a tech assessment. It’s a clear-eyed, comprehensive look at your IT environment that reveals risks, compliance gaps, and opportunities to strengthen your defenses.
For organizations in regulated industries, a tech assessment isn’t just a nice-to-have, it’s the foundation for every step that follows on your IT roadmap. Read more.