Industries We Serve
World Class IT Support & Service
Real People. Right Now.
About Locknet® IT Services
From the first hello, the Locknet® team is dedicated to serving you and your needs.
Real People. Right Now.
From the first hello, the Locknet® team is dedicated to serving you and your needs.


Updated December 8, 2025
A pharming attack is a sophisticated cyberattack that silently redirects users from a legitimate website to a spoofed, malicious one - often without any clicking, phishing email, or user error. While phishing relies on deception to lure someone into taking an action, pharming alters the path between the user and the website itself.
With today’s rise in Domain Name System (DNS) manipulation, DNS cache poisoning, and AI phishing attacks, pharming has evolved into a major threat to any organization handling sensitive data.
Modern pharming attacks are engineered to steal login credentials, financial information, session cookies, and identity data. In some cases, they also deploy malware for long-term access.
Although both attacks aim to steal information, they operate differently:
In short, phishing targets people and pharming targets the infrastructure that directs people online. A pharming attack doesn’t necessarily need a phishing lure to get started. Instead, it just plants a seed you don’t know is there and harvests the user’s information later.
Pharming is a sophisticated cyber-attack that requires more work from the cyber criminals, making them less common than phishing attacks. None the less, the impact of a pharming attack can be significant. Typically, pharming uses one of the following techniques:
Once users are redirected to fraudulent websites, pharmers obtain personal information. The attackers then either use the credentials for financial fraud or account access. They may also sell the information to other criminals on the Dark Web.
AI has changed the cybersecurity landscape in ways that directly amplify pharming threats:
The combination of DNS manipulation + AI phishing + advanced spoofing makes pharming attacks more scalable and more difficult to detect.
So, what does a pharming attack really look like? Here are just a few notable real-world examples of pharming.
These incidents highlight how pharming can exploit both consumer hardware and enterprise infrastructure.
Given the growing sophistication of pharming attacks, it’s essential for organizations to take proactive steps to defend their networks and users. Below are some effective strategies that can help reduce the risk of falling victim to these threats.
Modern Zero Trust browser controls:
Modern browser security controls stop pharming even when DNS is compromised.
Most pharming malware exploits outdated software. Consistent patching reduces the attack surface significantly.
Even if credentials are stolen, MFA can stop attackers from gaining access.
Verify certificates and block sites with invalid or suspicious SSL certificates.
Conduct regular security awareness training so employees know how to:
Human awareness remains one of the strongest defenses.
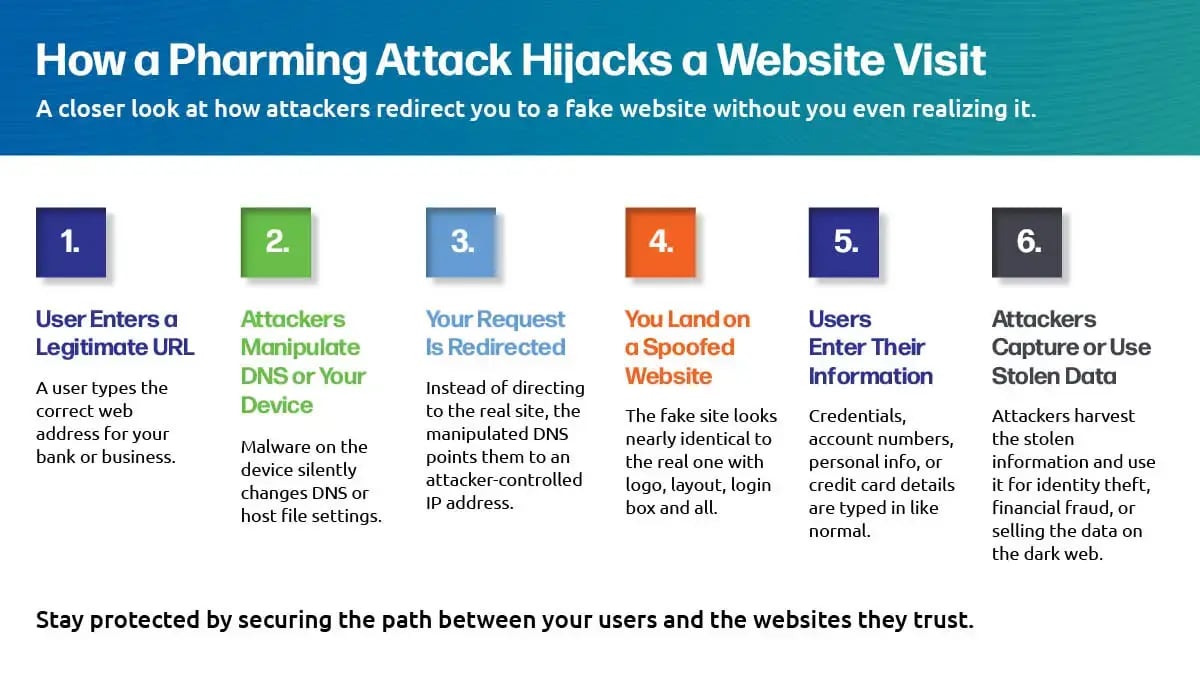
A pharming attack is a cyberattack that redirects users from a legitimate website to a fraudulent one - often using DNS manipulation, DNS cache poisoning, or malware to alter system routing.
DNS manipulation corrupts the translation between domain names and IP addresses. When users attempt to load a legitimate site, the manipulated DNS directs them to a spoofed site controlled by attackers.
AI enables attackers to create convincing phishing emails, realistic spoofed websites, and automated credential-harvesting tools which make pharming campaigns more scalable and harder to detect.
Organizations can prevent pharming by securing their DNS infrastructure, enforcing Zero Trust browser controls, patching systems, enabling MFA, and maintaining ongoing security awareness training.
Pharming attacks are evolving quickly, but with modern DNS protections and smarter web security controls, organizations can stay a step ahead. Strengthening the path between your users and the websites they trust is one of the most effective ways to shut down these threats before they cause real harm.
Ready to strengthen your organization's defenses? Partner with Locknet for comprehensive cybersecurity solutions and expert guidance to protect against evolving threats like pharming. Contact our cybersecurity team today to schedule a consultation and ensure your business stays secure.
Cybersecurity

Onalaska, WI Waterloo, IA Wausau, WI Eau Claire, WI Burnsville, MN
You are now leaving locknetmanagedit.com. Please check the privacy policy of the site you are visiting.