Industries We Serve
World Class IT Support & Service
Real People. Right Now.
About Locknet® IT Services
From the first hello, the Locknet® team is dedicated to serving you and your needs.
Real People. Right Now.
From the first hello, the Locknet® team is dedicated to serving you and your needs.


Updated December 15, 2025
Businesses are more vulnerable than ever to a persistent and evolving mix of cyber threats. From data breaches to ransomware attacks, the stakes are high and the consequences far-reaching. To fortify their defenses, organizations must adopt a layered security strategy, now strengthened by modern Zero Trust principles, that blends technical and organizational controls to stay ahead of attackers.
Layered security, or defense in depth, uses multiple barriers to protect systems, data, and users. Rooted in the military principle that breaching several defenses is far more difficult than overcoming one, this approach spans physical safeguards, network and application protections, and user-centric controls.
Today, layered security aligns closely with Zero Trust Architecture, which assumes no user, device, or system is trustworthy by default. Together, these concepts reinforce a more resilient, adaptive cybersecurity posture.
Technical controls are the foundation of your IT environment, focusing on securely configuring systems and deploying tools that reduce or detect risk. Increasingly, these tools support Zero Trust Security by enforcing verification at every step and limiting implicit access.
Firewalls establish essential traffic filtering, while XDR provides real-time threat monitoring and response across your environment. These controls form core layers of defense but also complement Zero Trust by reducing blind spots and continuously validating activity.
Antivirus tools and vulnerability scanners act as the immune system of your digital infrastructure. By detecting malware and identifying weaknesses, they help eliminate risks before they can be exploited which is a valuable complement to Zero Trust security models.
Secure, off-site backups ensure data resilience, while encryption renders sensitive information unreadable to unauthorized parties. Within a Zero Trust framework, encryption supports the principle that data should remain protected even if perimeter defenses are bypassed.
MFA adds essential identity proof beyond passwords, significantly reducing unauthorized access. Identity management is a core requirement of Zero Trust, and MFA ensures users are continuously validated rather than trusted by default.
Organizational controls cultivate a security-first mindset and protect stakeholder trust. These cultural and procedural layers reinforce technical defenses and align naturally with Zero Trust principles centered on accountability and verification.
Human error contributes to many security incidents. Regular training supported by simulated testing helps employees recognize threats such as phishing and follow secure practices. Security education training aligns with Zero Trust by promoting constant vigilance.
Limiting user access based on job responsibilities minimizes risk. Enforcing the principle of least privilege directly supports Zero Trust, which requires users and systems to have only the access necessary and nothing more.
Despite robust defenses, incidents can still occur. Clear plans ensure swift action, minimized downtime, and rapid recovery. Within a Zero Trust approach, response plans emphasize visibility, containment, and continual improvement.
Routine evaluations of controls and policies help identify gaps early. These assessments strengthen both layered security and Zero Trust by ensuring defenses remain current, effective, and measurable.
Together, these organizational controls lay the groundwork for a resilient security posture. As we examine the advantages of layered security, it becomes clear how these measures interconnect to provide comprehensive protection.
Integrating technical and organizational controls forms a complete security ecosystem. When paired with Zero Trust Architecture, this framework protects not only technology but the human and process layers that attackers often exploit.
Cyber threats evolve quickly. Layered defenses combined with Zero Trust’s continuous validation allow organizations to adapt, update controls, and maintain vigilance across users, devices, and networks.
Regulatory requirements increasingly emphasize access controls, encryption, and demonstrable security practices. Layered security and Zero Trust work together to support compliance while strengthening overall resilience.
To illustrate how these concepts work together in practice, the following infographic presents a timeline of a typical day under a layered security and Zero Trust approach.
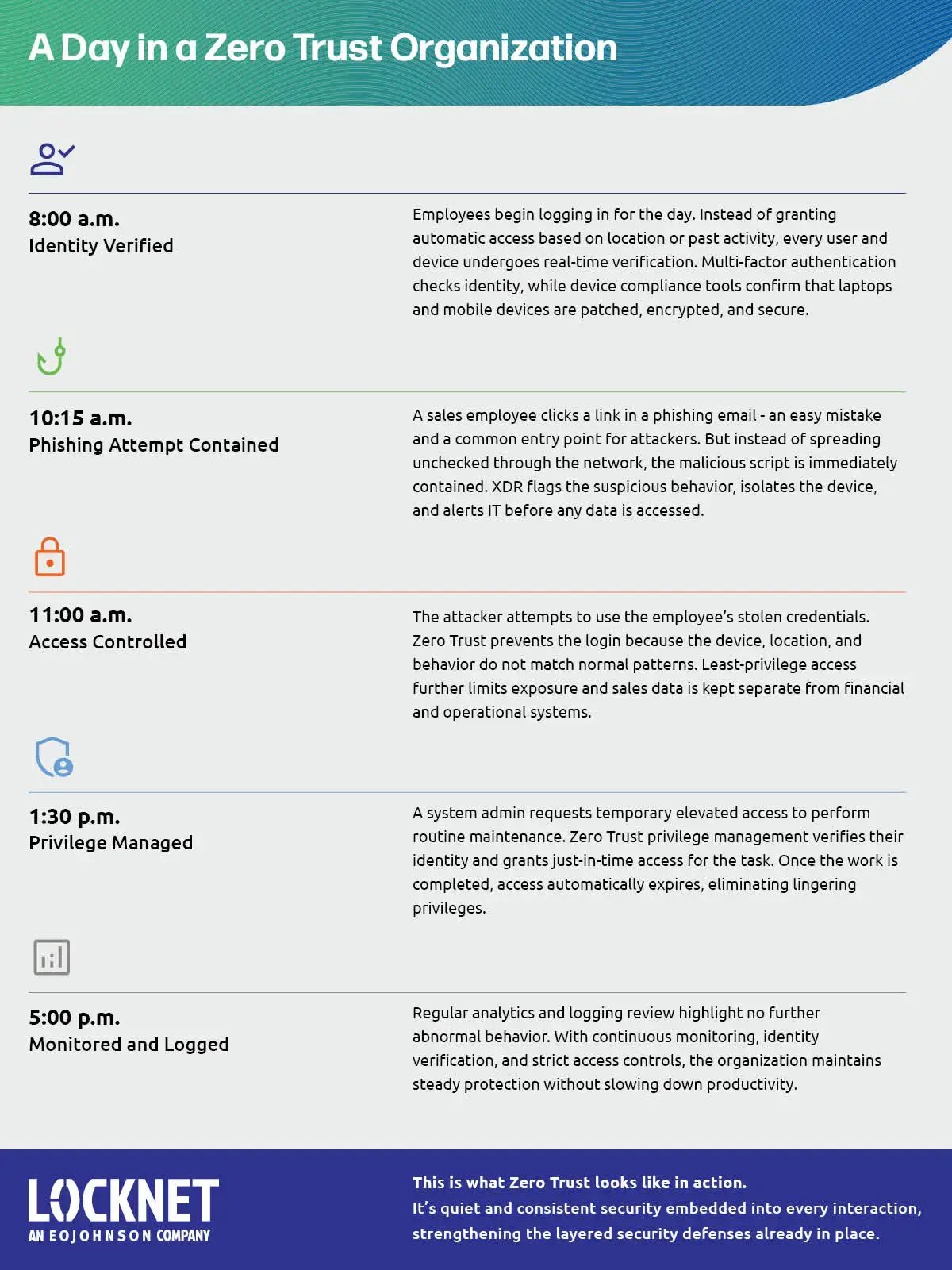
Layered security is a strategy that uses multiple protective controls, technical and organizational, to reduce risk. If one layer falls, others continue to protect systems and data.
Zero Trust strengthens a layered security approach by assuming no user or device is trusted by default. It requires continuous verification, least-privilege access, and strict control of data movement.
Cyber threats target different points, including users, networks, applications, and data. Multiple layers ensure that a single vulnerability does not lead to a full compromise, improving resilience and limiting damage.
Layered security provides broad protection by ensuring that if one layer is compromised, others remain intact. When enhanced with Zero Trust principles, this strategy becomes even more effective at minimizing risk and preventing breaches.
The team at Locknet can assess your environment and help you build the technical and organizational layers essential for a modern cybersecurity program. Our Keysuite offering delivers a comprehensive set of technical controls for organizations committed to strong security practices. And now, our Zero Trust Solution extends that protection even further by applying continuous verification and least-privilege principles across your environment.
If you're unsure about the strength of your current defenses, partnering with a Managed Security Service Provider for a thorough security assessment is an ideal first step toward a Zero Trust-aligned, defense-in-depth strategy. Contact us to learn more.
Cybersecurity

Onalaska, WI Waterloo, IA Wausau, WI Eau Claire, WI Burnsville, MN
You are now leaving locknetmanagedit.com. Please check the privacy policy of the site you are visiting.