Industries We Serve
World Class IT Support & Service
Real People. Right Now.
About Locknet® IT Services
From the first hello, the Locknet® team is dedicated to serving you and your needs.
Real People. Right Now.
From the first hello, the Locknet® team is dedicated to serving you and your needs.


Small healthcare clinics are prime targets for cybercriminals because they manage high-value patient data but often lack dedicated IT security staff. Hackers know these clinics face compliance pressures, outdated systems, and limited budgets which make them easier to exploit. The good news? Proactive cybersecurity measures like endpoint detection, data leak prevention, and managed IT support dramatically reduce risk and help protect patient trust.
Cybercriminals recognize that small clinics handle the same sensitive information as large hospitals such as names, birthdates, insurance details, and medical records. However, clinics often do not have the robust cybersecurity measures that larger institutions possess.
Many independent clinics depend on small internal IT teams or outsource to third-party vendors who may lack expertise in healthcare compliance. With limited budgets, complex HIPAA requirements, and outdated infrastructure, these clinics face significant vulnerabilities. Cybercriminals exploit these weaknesses, targeting clinics with ransomware and phishing attacks. In short, hackers aren’t just looking for big fish - they’re looking for easy ones.
The most common types of cyberattacks facing small clinics include:
Each of these attack types can lead to massive disruptions in patient care, loss of trust, and costly downtime.
But understanding the different types of cyberattacks is only half the battle. The infographic below illustrates how hackers typically infiltrate small healthcare clinics, step by step, and where proactive defenses can stop them.
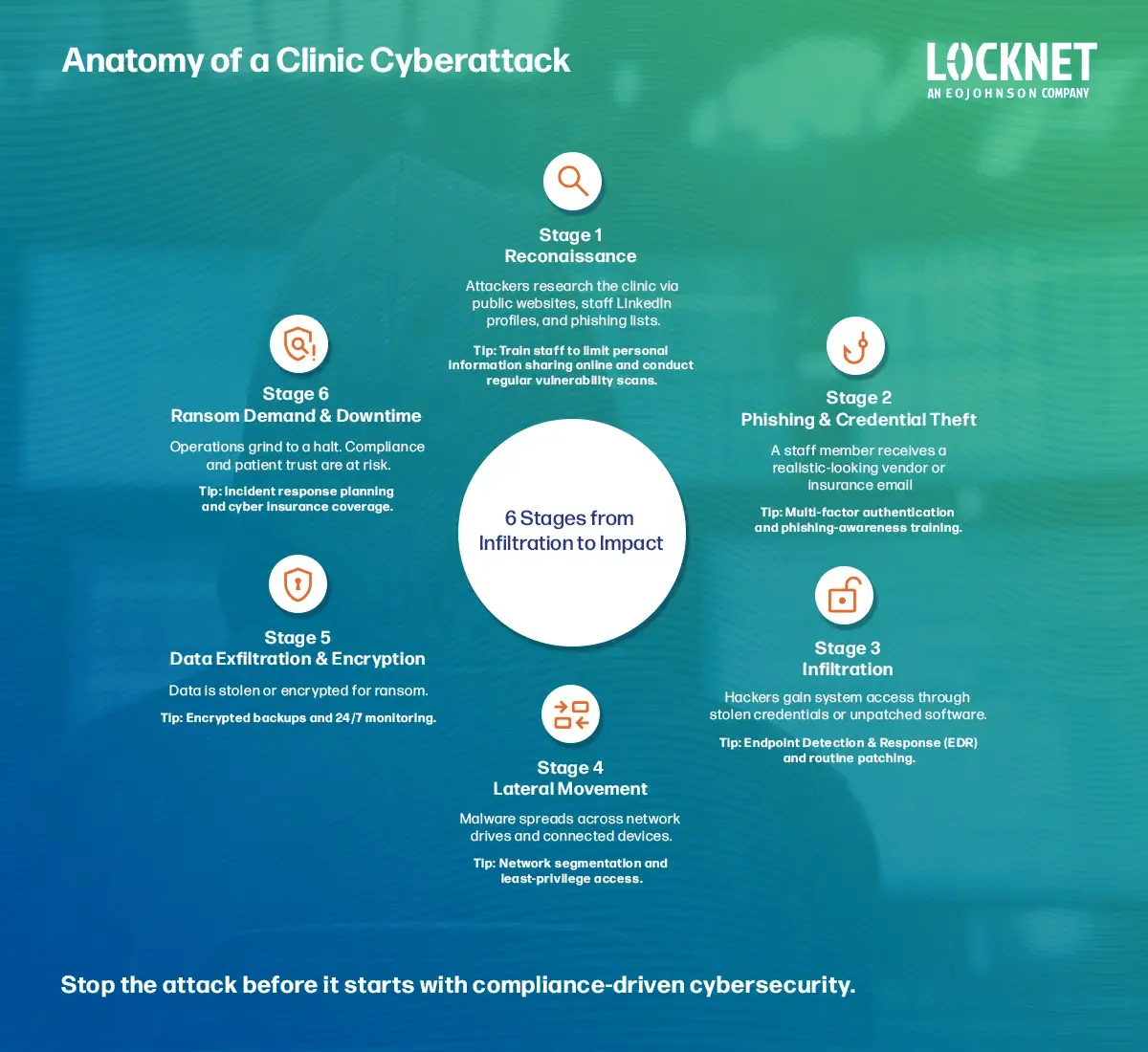
What Happens: Attackers research the clinic via public websites, staff LinkedIn profiles, and phishing lists.
Prevention Tip: Train staff to limit personal information sharing online and conduct regular vulnerability scans.
What Happens: A staff member receives a realistic-looking vendor or insurance email.
Prevention Tip: Multi-factor authentication and phishing-awareness training.
What Happens: Hackers gain system access through stolen credentials or unpatched software.
Prevention Tip: Endpoint Detection & Response (EDR) and routine patching.
What Happens: Malware spreads across network drives and connected devices.
Prevention Tip: Network segmentation and least-privilege access.
What Happens: Data is stolen or encrypted for ransom.
Prevention Tip: Encrypted backups and 24/7 monitoring.
What Happens: Operations grind to a halt. Compliance and patient trust are at risk.
Prevention Tip: Incident response planning and cyber insurance coverage.
Too often, small clinics see cybersecurity as an IT issue, but it’s fundamentally a compliance, risk management, and reputation issue. Beyond the operational chaos, a data breach puts your clinic’s compliance standing at risk. The Health Insurance Portability and Accountability Act (HIPAA) requires covered entities to safeguard protected health information (PHI). A single violation can result in penalties ranging from $100 to $50,000 per record.
Even a minor security gap such as an unpatched system or unsecured device can trigger an investigation by the Office for Civil Rights (OCR). For healthcare administrators, failures not only threaten finances but also erode patient confidence and reputation.
Your clinic may be more exposed than you realize. Watch for these warning signs:
If any of these sound familiar, your clinic could already be on a hacker’s radar.
Knowing you’re a target is only the first step. Here’s how your clinic can build a stronger defense without overwhelming your staff or budget:
The Cybersecurity and Infrastructure Security Agency (CISA) also offers a dedicated resource hub for the healthcare and public health sector. Their toolkit includes checklists, threat alerts, and best practices to strengthen defenses against ransomware and phishing.
If your internal IT resources are stretched thin or compliance feels like a moving target, it’s time to explore partnering with a Managed Security Service Provider (MSSP). A trusted partner provides:
For clinics like yours, the right partnership is about more than technology — it’s about building a culture of security that evolves with your business.
A. To improve cybersecurity at your clinic with a limited budget, start with cost-effective basics like employee phishing training, multi-factor authentication (MFA), managed endpoint protection, and regular backups. Many MSSPs offer scalable plans tailored for smaller healthcare organizations.
A. Yes, small clinics should invest in cyber insurance. Cyber insurance can help cover breach response costs, legal fees, and downtime losses. However, insurers often require strong baseline security controls, like encryption and threat monitoring, before approving coverage.
A. Smaller clinics are attractive targets for hackers because they hold valuable patient data but often lack enterprise-grade defenses, making them both high reward and low effort targets for cybercriminals.
Cybersecurity is no longer optional for healthcare providers and small clinics can’t afford to wait until a breach happens to act.
Join our upcoming healthcare cybersecurity webinar to learn how clinics across the Midwest are building resilience through managed security, compliance alignment, and proactive defense strategies. Register today and take the first step toward securing your clinic, your reputation, and your patients’ trust.
Cybersecurity

Onalaska, WI Waterloo, IA Wausau, WI Eau Claire, WI Burnsville, MN
You are now leaving locknetmanagedit.com. Please check the privacy policy of the site you are visiting.