Industries We Serve
World Class IT Support & Service
Real People. Right Now.
About Locknet® IT Services
From the first hello, the Locknet® team is dedicated to serving you and your needs.
Real People. Right Now.
From the first hello, the Locknet® team is dedicated to serving you and your needs.


Updated February 16, 2026
For many organizations, data is viewed as an asset. It’s something to collect, store, and protect. But in today’s AI-driven world, not all data is helpful. In fact, some data quietly becomes a liability.
Legacy data is old, forgotten, or poorly governed information. It can act like a digital anchor, weighing down security efforts, increasing risk, and limiting an organization’s ability to move forward safely.
Understanding when data stops being an asset and starts becoming a risk is a critical step in modern cybersecurity and data management.
Legacy data refers to information created by outdated systems, applications, or business processes that are no longer actively used. This might include:
Over time, this data often becomes dark data, or information that is stored but no longer understood, monitored, or used. It sits in the background, unmanaged and largely invisible.
While some legacy data must be retained for legal or operational reasons, much of it remains simply because no one has asked an important question:
Why are we still keeping this?
As organizations adopt cloud platforms, automation, and AI tools, unmanaged data becomes more than clutter. It becomes risk exposure.
Legacy data can act as a digital anchor in several ways:
In other words, bad data doesn’t stay neutral. It actively creates problems.
In fact, there are several recent cases of companies incurring regulatory fines for the over-retention of data.
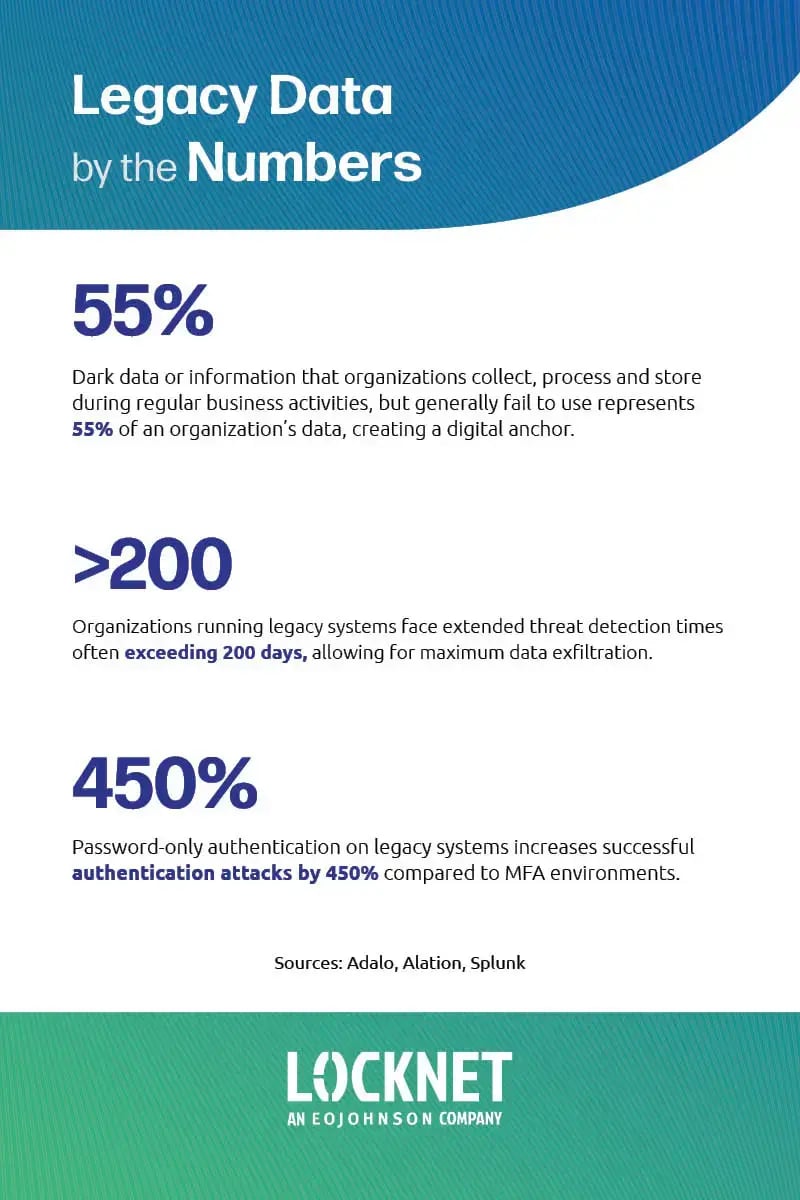
AI systems are only as good as the data they rely on. Legacy data, especially dark data, is often incomplete, outdated, or poorly classified.
When this data is used (intentionally or not) to train or inform AI systems, it can lead to:
Instead of accelerating innovation, legacy data can quietly undermine it. Clean, well-governed data enables AI to move faster. Dirty data slows everything down and raises agentic AI risk along the way.
Attackers don’t just look for what’s valuable today but also look for what might be valuable tomorrow.
Legacy data is especially attractive because:
As discussions around quantum readiness and future decryption evolve, organizations must consider a growing concern that data stolen today could be decrypted years from now.
Old data that seems harmless now may become highly sensitive in the future, especially if it includes personal data, proprietary research, or long-term contracts.
Strong data governance is a business responsibility. Let’s look at data management from an ESG (Environmental, Social, and Governance) perspective:
Managing legacy data thoughtfully supports broader organizational goals around sustainability, ethics, and transparency.
Zero Trust security principles operate under the assumption that no system or data should be trusted by default. Legacy data, however, poses a challenge to this framework, particularly when it remains poorly documented, broadly accessible, and outside the scope of modern access controls.
To apply Zero Trust concepts effectively to data, organizations must know precisely where their data resides, restrict access according to roles and actual need, and continuously assess which data should continue to exist. Without a clear understanding of the data environment, especially regarding legacy data, it is impossible to adequately protect valuable information.
There are a few key actions your organization can take to address legacy data now and in the future.
Do you know where all your data is and is it protected? Holding on to legacy data indefinitely carries inherent risks. Audit your legacy systems for forgotten data. Then record and track the risks identified to use them in the creation of a data hygiene program.
A fundamental component of data management is that data must be owned throughout its life with processes in place to ensure that data doesn’t become forgotten. Records retention also plays a key part in data governance. A sound record retention schedule establishes rules for the defensible disposal or archiving of data. It’s then possible to retire and decommission a legacy system and its associated data according to the parameters in place.
Your company should also have a standardized approach for application decommissioning that includes the associated data. If it’s necessary to retain the data, it should be archived on an alternate platform in accordance with your organization’s record retention schedule.
Merger and acquisition due diligence should include a clear understanding of data privacy roles, responsibilities, and processes. Review the systems you will be acquiring and develop a plan to address any data risks. Without this, the forgotten data of the company you are acquiring can make your organization vulnerable.
Backup data is only intended to be used for disaster recovery and should not be used as an archive for data retrieval. There should be detailed processes in place to overwrite or destroy backups that are beyond their retention period. When you keep backup data beyond its intended purpose, you are introducing unnecessary risk into your organization.
In addition to security risk mitigation, managing legacy data effectively can provide cost savings for organizations. There are many hidden costs associated with maintaining outdated systems and technologies, including system maintenance, data migration, and compliance-related expenses.
In an AI-driven world, data is power but only when it’s intentional, governed, and trusted. Legacy data doesn’t just sit quietly in the background. Left unmanaged, it becomes a digital anchor, slowing innovation, increasing risk, and creating future exposure. Organizations that treat data as both an asset and a responsibility will be better positioned to adapt, innovate, and stay secure for years down the road.
If you have questions on how to address your legacy data, reach out to Locknet’s team of managed IT and cybersecurity experts. We’re here to help.
Cybersecurity

Onalaska, WI Waterloo, IA Wausau, WI Eau Claire, WI Burnsville, MN
You are now leaving locknetmanagedit.com. Please check the privacy policy of the site you are visiting.